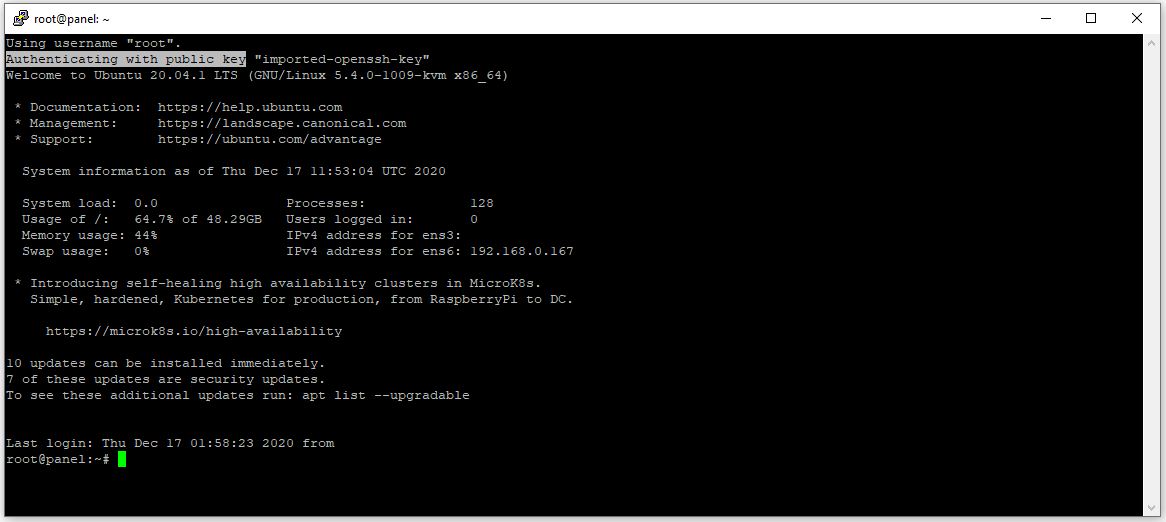
By default, the SSH service runs on port 22, but to prevent automated robots and malicious users from brute-forcing into your server, you should consider changing the default 22 SSH port with another randomly selected one..
To prevent incorrect server configuration, you should choose a port from the range of dynamic / private ports (i.e., 50012, 49911, 65530).
ICANN (The Internet Corporation for Assigned Names and Numbers) classifies communication ports into three categories:
0-1023 - System/well known ports 1024-49151 - User/registered ports 49152-65535 - Dynamic/private ports
To change the default port that the SSHD daemon listens to, you need to edit the configuration file using a text editor:
$ sudo nano /etc/ssh/sshd_config
Then look for the next line in the file:
# Port 22
Un-comment the line by removing the # sign before, then change with your new port:
Port 51655
Be careful not to forget this port, write it down somewhere or memorize it, because otherwise it will be quite difficult to find it and reconnect to the server!
To avoid completely locking yourself from your system, you should whitelist the port that you have specified above on your firewall
In order not to completely locking yourself from your system, you should whitelist the port you specified above on the firewall. If you are using UFW (Uncomplicated Firewal), use the following commands:
@ sudo ufw allow 51655/tcp @ sudo ufw reload
Once you have modified the SSHD daemon configuration file, you should restart the services to reload the new changes and make the port active.
$ sudo service sshd restart
P.S. Another additional layer of security is disabling password authentication and connecting to your server using key pair authentication. I use this method for servers that require more security!


Leave a Reply
Your email address will not be published. Required fields are marked *